Encryption with Self Encrypting Drive (SED)
An SED has a built-in encryption function and data can be encrypted by controlling the encryption function of an SED from the controller. An SED uses encryption keys when encrypting and storing data. Encryption keys cannot be taken out of the drive. Furthermore, because SEDs cannot be decrypted without an authentication key, information cannot be leaked from drives which have been replaced during maintenance, even if they are not physically destroyed.
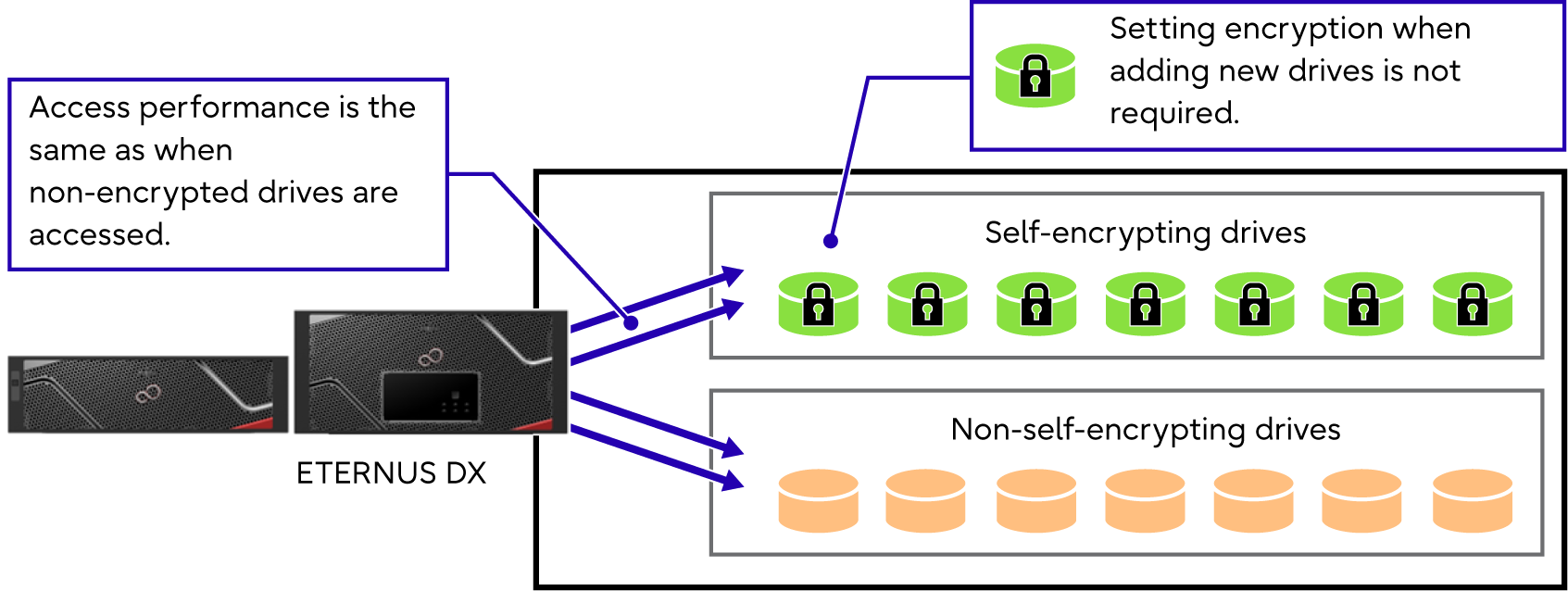
Once an SED authentication key is registered to an ETERNUS DX, additional configuration on encryption is not necessary each time a drive is added.
Data encryption by SED has no load on the controller for encryption process, and the equivalent data access performance to unencrypted process can be ensured.
The controller performs authentication by using the authentication key (common key) that is stored in the controller to access the drives. For the authentication key that can be registered in the ETERNUS DX, this key is automatically created by using the settings in ETERNUS Web GUI or ETERNUS CLI.
Only one unique SED authentication key is registered in each ETERNUS DX.
The firmware data encryption function cannot be used for volumes that are configured with SEDs.
The SED authentication key (common key) is registered at the time of shipping, regardless of whether an SED has been prepared.



