Firmware Data Encryption
The firmware in the ETERNUS DX has the firmware data encryption function. This function encrypts a volume when it is created, or converts a created volume into an encrypted volume.
Because data encryption with firmware is performed with the controller in the ETERNUS DX, the performance is degraded, comparing with unencrypted data access.
The encryption method can be selected from the world standard AES-128, the world standard AES-256, and the ETERNUS Original Encryption method. The ETERNUS Original Encryption method that is based on AES technology uses an ETERNUS original algorithm that has been specifically created for ETERNUS DX storage systems. The ETERNUS Original Encryption method has practically the same security level as AES-128 and the conversion speed for the ETERNUS Original Encryption method is faster than AES. Although AES-256 has a higher encryption strength than AES-128, the Read/Write access performance degrades. If importance is placed upon the encryption strength, AES-256 is recommended. However, if importance is placed upon performance or if a standard encryption method is not particularly required, the ETERNUS Original Encryption method is recommended.
Encryption is performed when data is written from the cache memory to the drive. When encrypted data is read, the data is decrypted in the cache memory. Cache memory data is not encrypted.
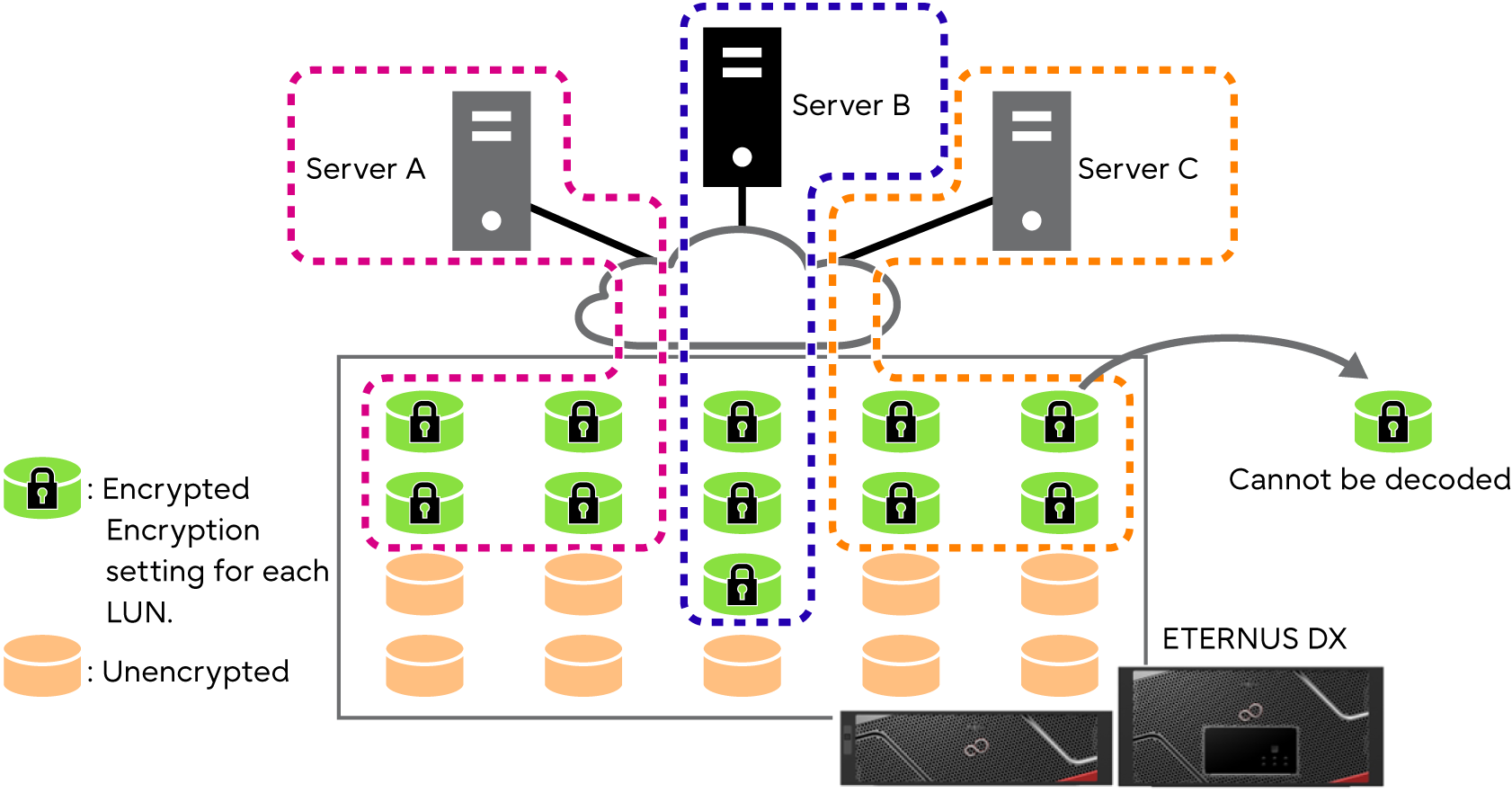
For Standard volumes, SDVs, SDPVs, and WSVs, encryption is performed for each volume. For TPVs and FTVs, encryption is performed for each pool.
Before the firmware data encryption function is used, the encryption mode of the ETERNUS DX must be enabled (*1).
*1 : This means that the encryption mode is set to "ETERNUS Original Encryption" or "AES".
The encryption method for encrypted volumes cannot be changed. Encrypted volumes cannot be changed to unencrypted volumes.
To change the encryption method or cancel the encryption for a volume, back up the data in the encrypted volume, delete the encrypted volume, and restore the backed up data.
The encryption method of a firmware encrypted pool (TPP or FTRP) cannot be changed regardless of whether the volume is registered to a pool.
It is recommended that the copy source volume and the copy destination volume use the same encryption method for Remote Advanced Copy between encrypted volumes.
When copying encrypted volumes (using Advanced Copy or copy operations via server OS), transfer performance may not be as good as when copying unencrypted volumes.
SDPVs cannot be encrypted after they are created. To create an encrypted SDPV, set encryption when creating a volume.
TPVs cannot be encrypted individually. The encryption status of the TPVs depends on the encryption status of the TPP to which the TPVs belong.
FTVs cannot be encrypted individually. The encryption status of the FTVs depends on the encryption status of the FTRP to which the FTVs belong.
The firmware data encryption function cannot be used for volumes that are configured with SEDs.
The volumes in a RAID6-FR RAID group cannot be converted to encrypted volumes.
When creating an encrypted volume in a RAID6-FR RAID group, specify the encryption setting when creating the volume.



